In my previous post, we went though defining XACML policies for web application. Now i am going to try out the scenario, that is defined in that blog post, with third approach. i.e. By using “getEntitledAttributes” method in Entitlement Service API of Identity Server. Identity Server is an open source XACML engine that supports XACML 3.0. “getEntitledAttributes” is a method which can be used to retrieve entitled attributes for given user or role. This API method is specific to Identity Server and you can read more details about this from here
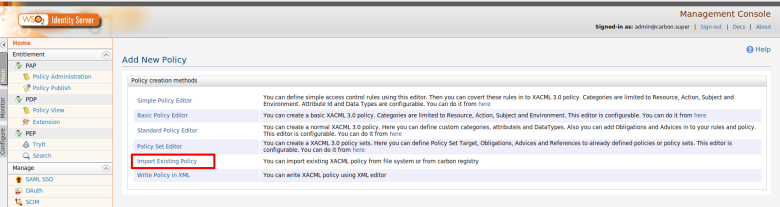
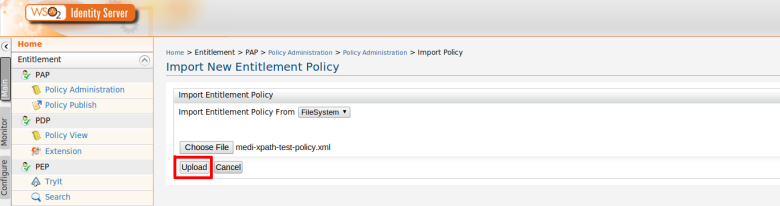
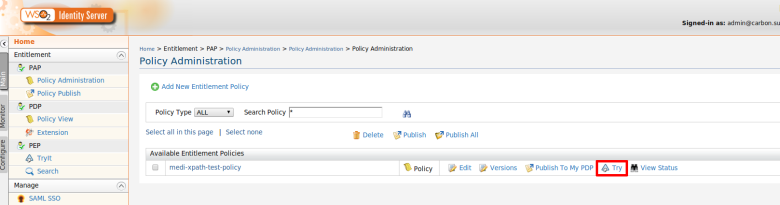
Step 1. You need to upload and publish these policies in to the XACML PDP as enabled policies. You can find more details from here.
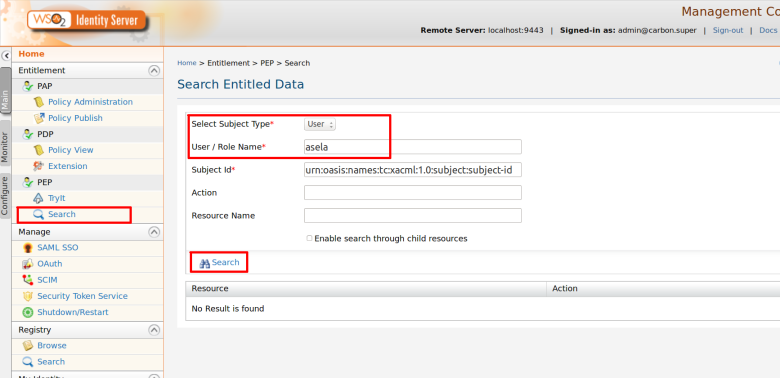
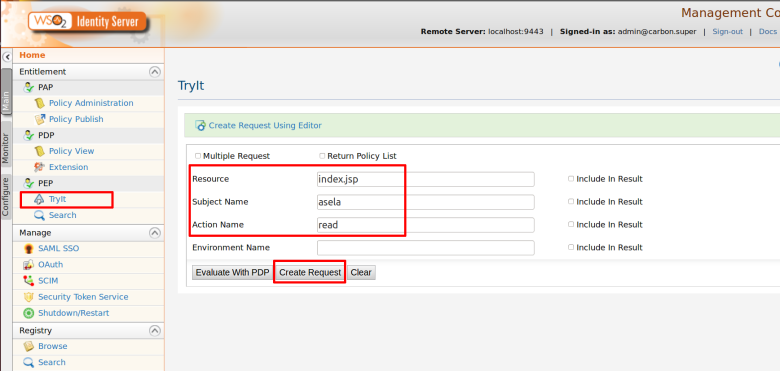
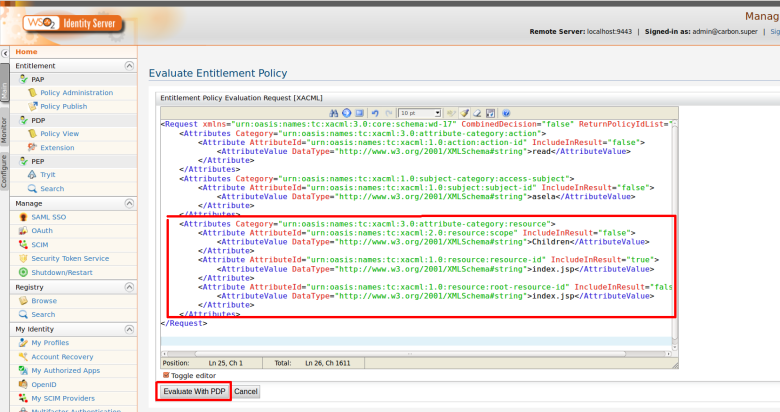
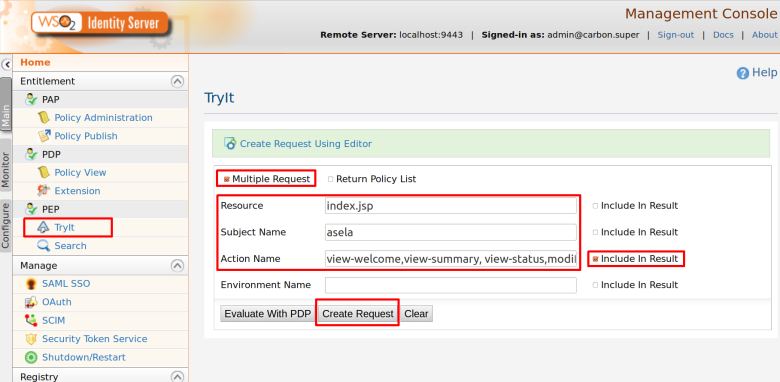
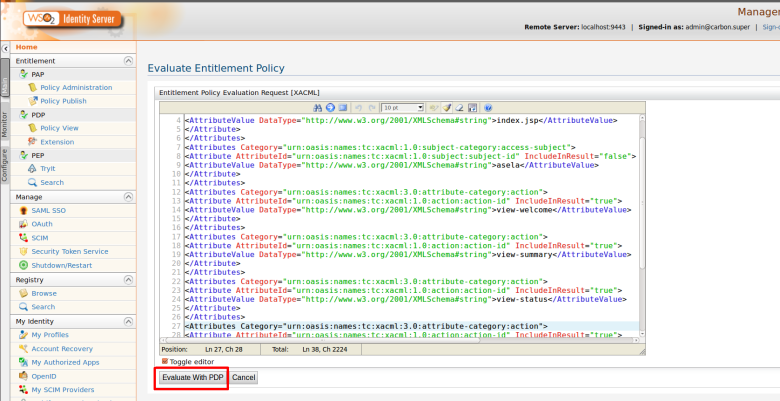
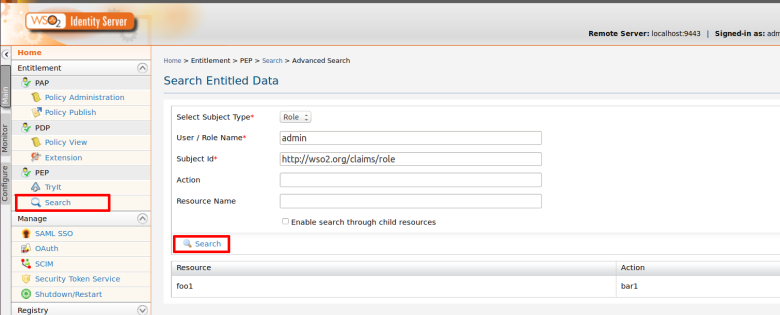
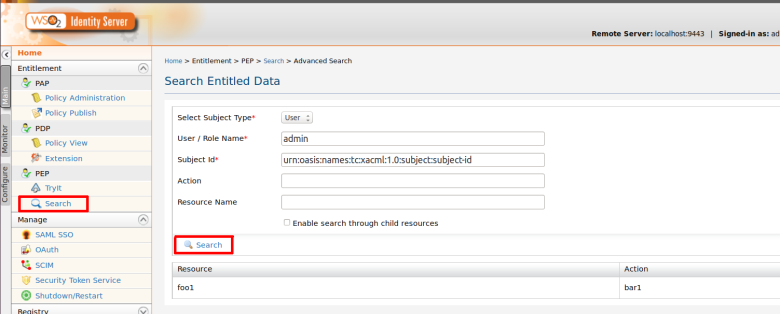
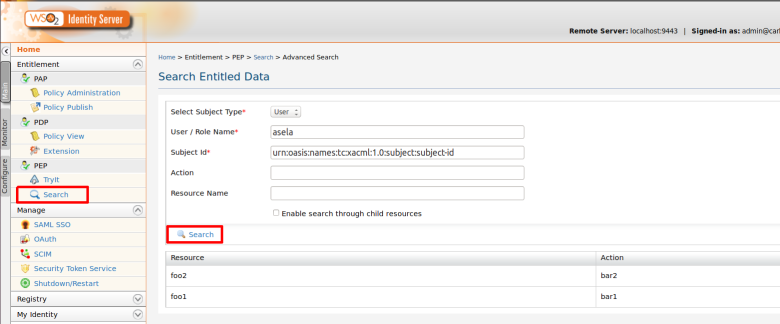
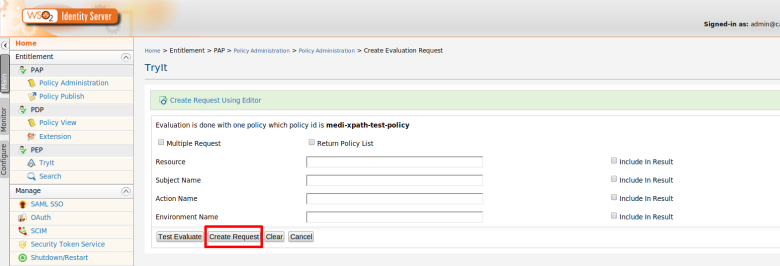
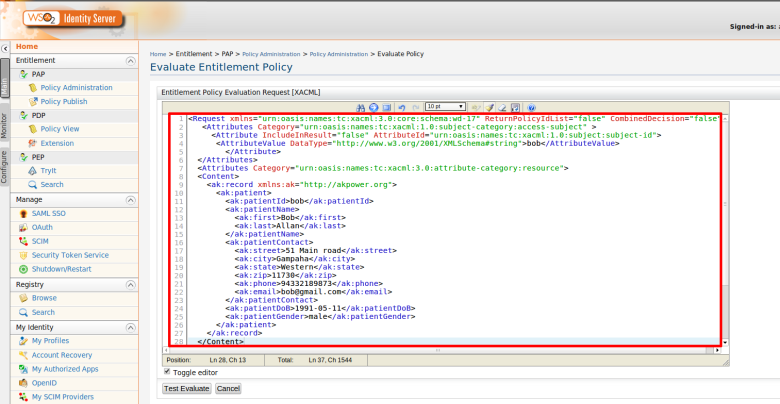
Step 2. Use PEP Search tool to invoke the PDP (Or else you can invoke “getEntitledAttributes“ method of the PDP web service API using a SOAP client such as SOAP UI )
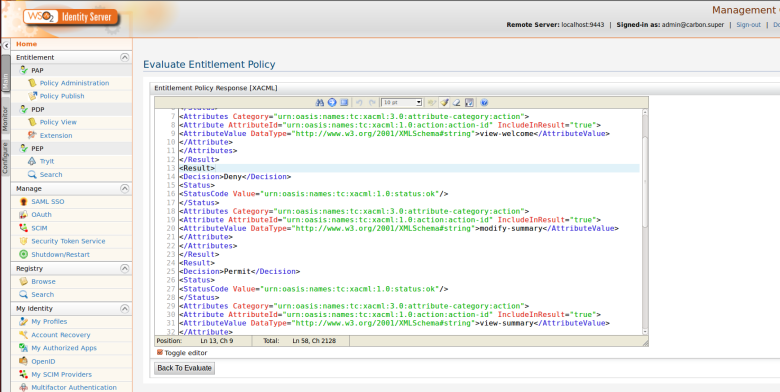
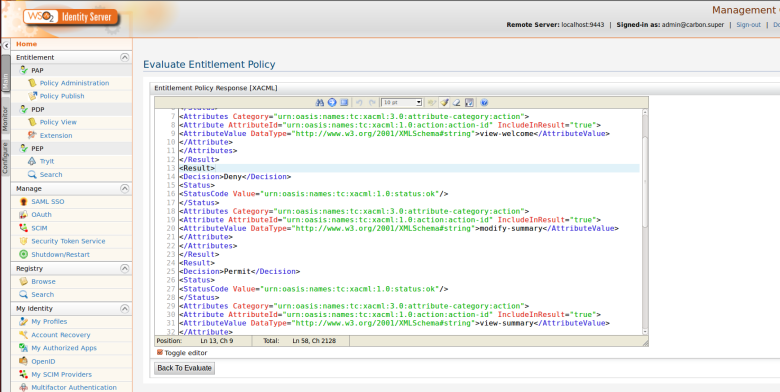
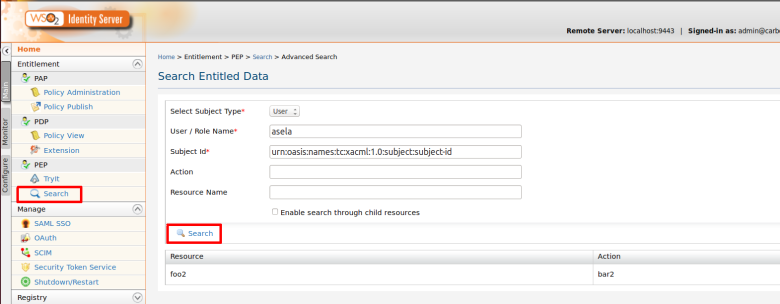
Here i am going to retrieve entitled resources for given user called “asela” that has been assigned to “InternalUsers” role
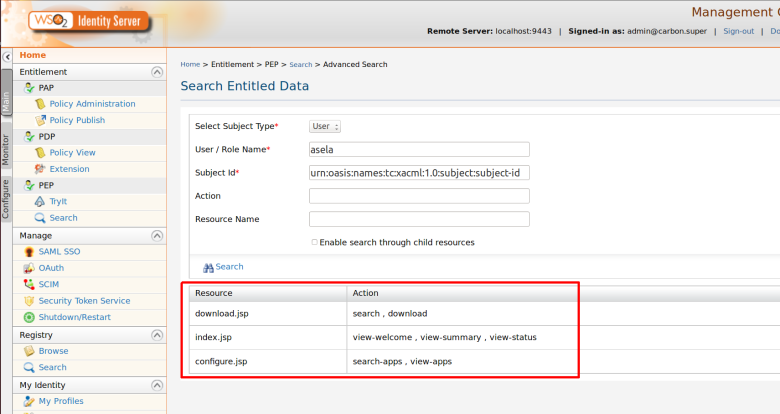
Step 3. You can see the entitled attributes values. i.e resources and actions names.
As mentioned in my previous blog post, This is not an efficient API method. Due to two reasons, If i summarized them again
- This method internally creates all possible XACML requests and they are evaluated with PDP.
- Attribute values are retrieved by parsing policies to create XACML requests.
In this scenario, As we know the actions set that is related to each web page, Therefore we can feed the action set in to the PDP. Then PDP does not want to extract attribute values from XACML policies and also It can be avoided the creating of some unwanted XACML requests. There is a method that you can extend to feed attribute values that you wish
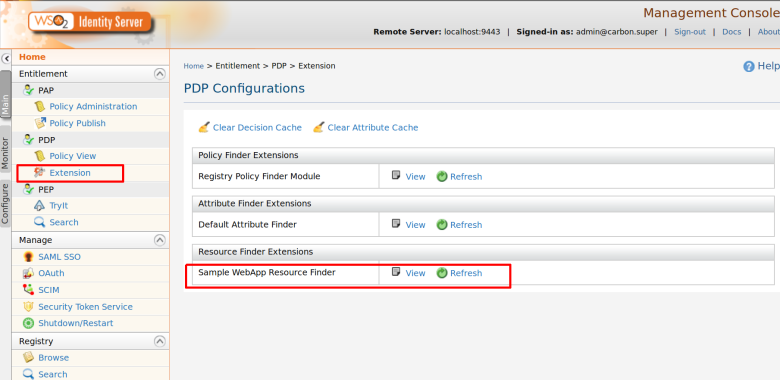
You can find the sample implementation from here that is an extended version of default policy finder module. Here “getSearchAttributes” has been extended to feed the resource and actions names You can try out this scenario with this implementation. Please go through following additional steps. Here i have found that, number request that have been created internally is reduced by half. With default implementation, If was around 61 XACML requests and with sample implementation it is 32 XACML requests. That is some improvement. Also It is not parsing XACML policies which is also good for performance.
Step 1. Write a New Policy Finder module by extending the default “RegistryPolicyStoreManageModule”. Please find the “SamplePolicyAttributeRetriever” class from here.
Step 2. You need to create a jar file. You can build the project using maven 3 and create the jar file.
Step 3. Copy created org.xacmlinfo.xacml.search.extension-1.0.0.jar in to <IS_HOME>/repository/components/lib directory
Step 4. Copy any dependency libraries for PIP module to <IS_HOME>/repository/components/lib directory.
Step 5. Open the entitlement.properties file which can be found at <IS_HOME>/repository/conf/security directory and register your new policy finder module. Following is the sample configuration and i have removed the default policy finder and have added new extended policy finder.
PDP.Policy.Finder.1=org.xacmlinfo.xacml.search.extension.SamplePolicyAttributeRetriever
Step 6. Restart the Server if already has been started.
You can actually debug this sample code by starting the WSO2 Identity Server in the debug mode as follows
wso2server.sh –debug 5005 (UNIX) or wso2server.bat –debug 5005 (Windows)
Then you can clearly see how the method in “SamplePolicyAttributeRetriever” are called by the PDP.