In my previous posts, we tried the federation authentication with WSO2IS and other third party identity provider such as Salesforce, Google IDP, Shibboleth and so on. You can find them from here
In this post, we are trying to understand,, how to configure multiple federated IDPs with given service provider.
Let assume that we have already configure Google Salesforce and Shibboleth as federated IDP.
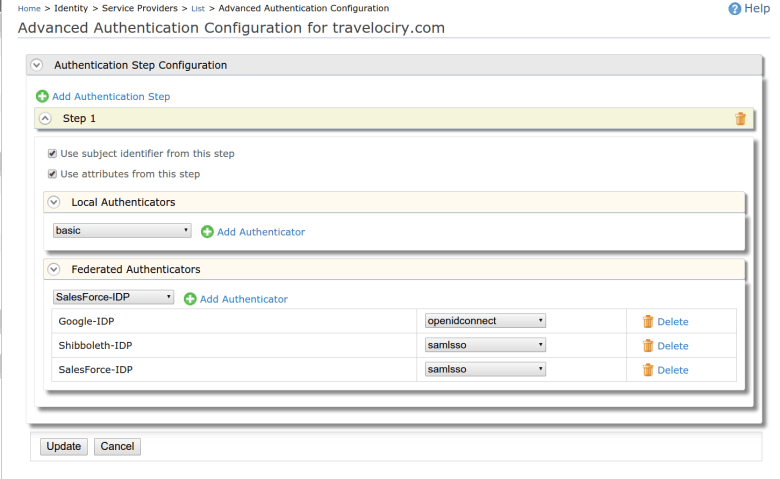
Step 1. Go to “Advance Configuration” of the Local and Outbound authentication configuration.
Step 2. Select the Google, Salesforce and Shibboleth IDP in given step as followings.
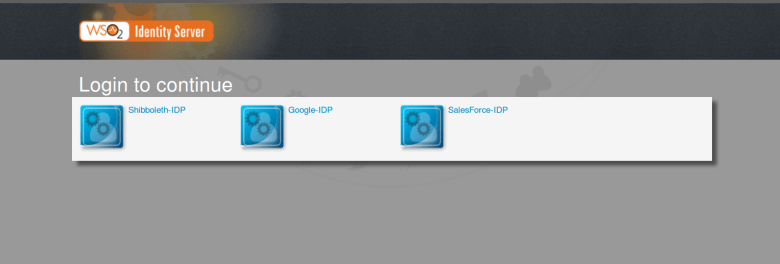
Step 3. Try to login to Service provider. Then end user would be redirected to WSO2IS
Step 4. SSO login page of WSO2IS would be shown as following. End user needs to select the desired IDP out of three IDPs listed in here.
Say; Service provider already knows the IDP which end user is belonged or which end user must be selected. Then, there is no need to select the IDP by the end user using WSO2IS login page.
You need to go through following steps to achieve this.
Step 1. Define a “Home Realm Identifier:” value for each Federated IDP.
As an example, for Google-IDP, we can define the value as “googleIdp”
Step 2. Service provider must sent the “Home Realm Identifier” value as the query parameter in the authentication request.
As Service provider already knows the IDP, Then SP can send the “Home Realm Identifier” value for given IDP using “fidp” query parameter.
If it is google IDP, Then value must be
fidp=googleIdp
Step 3. WSO2IS finds the IDP related to the “fidp” value and redirects the end user to the IDP directly rather than showing the SSO login page.
Thanks for reading…!!!